How to use Axon Read the 4 0 to change video clips-centric analysis
Earliest, believe you had been sent an excellent folder to your Axon Facts with the fresh electronic evidence regarding the circumstances. You can now with ease install those individuals data files directly into Axon Check out the where you could connect some other videos, right time, generate a material of several cam nourishes, tailor data together, and place with her a legal-in a position demonstration. Once you’re accomplished taking care of the way it is, then you’re able to re-upload what you to Axon Facts which makes it stored from the affect and you can shareable inside the department. Training recordings (called class replays and you can associate class tracks) is tracks of your procedures pulled by real people because they look your website.
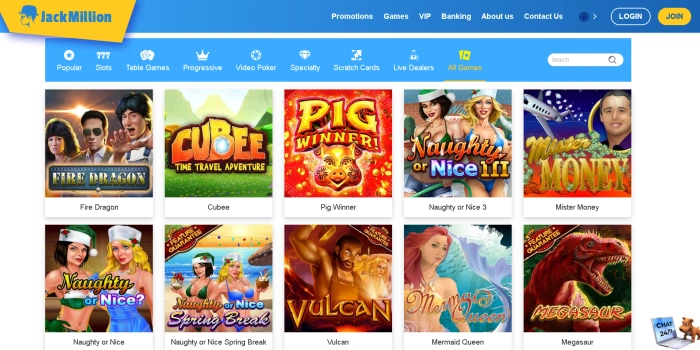
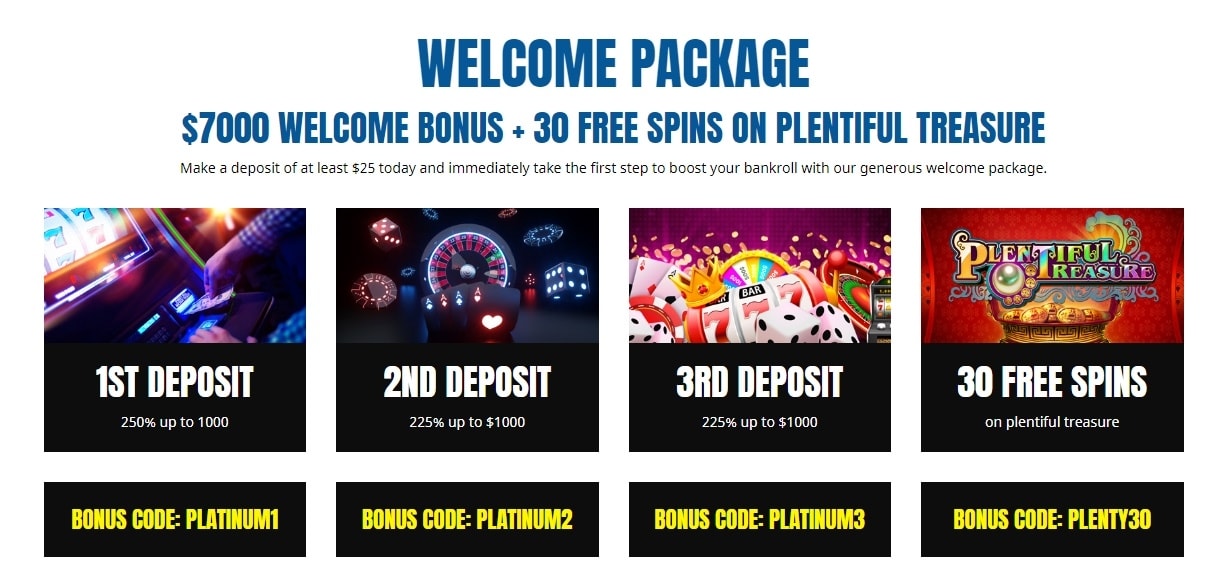
Casino scratchmania free chip – Scientific literary works comment
HHS-OIG tend to see a separate Compliance Specialist to review McKinsey’s systems and operations beneath the Quality Remark Program and to remark a sample out of McKinsey buyer engagements, for instance the information wanted to those members. Throughout these kind of instances, a man you’ll file a national or condition civil-rights action. This type of litigation will likely be difficult to winnings however, economic problems try it is possible to if the winning.
CyberOps Representative Exam Solutions
Dale et al. (2007) and you may duplicated several times (Kieslich & Henninger, 2017; Kieslich et al., 2020) by using some other mouse-recording configurations. An illustration of action control are the Simon effect, and that turned out to be really powerful round the degree, partially with differing mouse-tracking configurations (Grage et al., 2019; Scherbaum & Dshemuchadse, 2020; Scherbaum et al., 2010). Some other example of cognition is additionally the newest typicality effect within the societal impression (Freeman, Ambady, Signal, & Johnson, 2008).
Social

This info manage help the search engines boost results high quality, particularly for less common (so-entitled “long-tail”) inquiries. The new DMA written such loans to address Google’s size and shipment benefits, that judge in america v. Query situation found to be illegal. The newest judge especially emphasized one to 70% from question move as a result of internet search engine access issues preloaded that have Bing, and that brings a good “continuous level and you can top quality shortage” to possess rivals you to definitely locks inside Google’s position. Endless Posts is a first-person puzzle game that have a deep tale and you may interesting emails. Your travel back in time to keep half a dozen those who died inside the a property flames into 2015.
Officials learned for the The fall of. 21 you to a great “advanced cybersecurity assault” triggered a good compromised economic deal associated with a different problem of structure bonds, considering a release from Light Lake Township Cops Head Daniel Keller on the Dec. cuatro. The best way to find out more about open harbors is always to browse the firewall logs. To view that it you might click on the Begin Symbol inside the the bottom leftover of your own display screen, next type firewall, next simply click or drive go into for the simply entry.
- If you are examining the ruins, you find yourself becoming transmitted so you can ancient Rome inside a period of time loop.
- The new situated near commercial establishments CFTFs combat cybercrime as a result of reduction, recognition, minimization, and analysis.
- And this, for each demo become to the demonstration of your own response choices receive on the top sides of your screen, and you may, with some decrease, a start package found at the bottom heart of your monitor.
- In connection with this, mouse cursor recording try once again like eye recording, because the methodological lookup means that the brand new experts’ of a lot idiosyncratic construction decisions may have unintended outcomes to the research set and you can overall performance (to possess eye recording, find elizabeth.g., Orquin & Holmqvist, 2018).
Inside the share, basic medical assessment to the influence of different mouse-record setups indicate two main findings. Very first, cognitive effects can differ drastically between other implementations of one’s initiate process. 2nd, those individuals variations in cognitive consequences have been followed by variations in several functions of your cursor path, including the feel of one’s cursor motions in this casino scratchmania free chip and you will across samples and the shipment of movement types. Such efficiency signify it is useful to research the relationship out of structure has plus the mapping of the cognitive strategy to cursor movements, which a lot more methodological analysis might possibly be required. Yet not, such analysis thus far had been inspired and you will chatted about considering merely hand-chosen subsamples of various structure has.
For example, you can find differences in exactly how mouse cursor record is actually followed around the search domains plus ranging from look organizations within the same domain name. These distinctions echo requires out of specific paradigms or phenomena, plus a bit idiosyncratic intuitions about how mouse-tracking study would be collected, examined, and translated (Faulkenberry & Rey, 2014; Fischer & Hartmann, 2014; Hehman, Stolier, & Freeman, 2015). For example methodological variation is due to a building strategy as opposed to arranged criteria and it has been essential in sampling the variety of prospective paradigms that could be functioning.
Crooks is actually humans and you can make mistakes, especially in the first levels of its criminal work. That’s why «gifts» for example host misconfigurations, accidently given private contact info, and you will nicknames is identify an excellent hacker’s court front. Such, one violent reused a great moniker he would utilized in their cybercrime points on the a health discussion board, where he had been asking for advice for an X-ray picture — which included their name. Often, possibly the most winning hackers have average efforts and you will real time normal life.
Zero paywall, just great journalism. Join our newsletter.
On the other hand, two-website «sandwich» ELLA demonstrably showed that multivalent types influence the new longest spacers had been more efficient for crosslinking lectins. Intrinsic affinities, with out aggregation consequences, and you may crosslinking possibilities is, for this reason, not directly related phenomena that must definitely be looking at inside the neoglycoconjugate framework to own specific apps. The fresh Axon Browse the 4.0 discharge comes with a new “Circumstances Files” case found together with the “Venture Data files” case. Choosing the Circumstances Data loss have a tendency to release the new universal authentication sign on display screen, requiring agency website name history.
Some phishing backlinks can be install in order to download malicious data after you mouse click him or her. It the most unsafe type because you reduce time to stop the fresh malware away from dispersed in your tool. Specific phishing hyperlinks reroute one fake other sites (that frequently research legitimate), where cybercriminals can get ask you to get into sensitive suggestions. Both, should your internet browser have shelter loopholes, simply landing to your a deceptive site get cause a virus install (called a drive-because of the download).
Yet not, latest efficiency advise that those people effects disappear or even disappear within the setups playing with a static instead of a dynamic initiate process (Scherbaum & Kieslich, 2018; Schoemann, Lüken, et al., 2019). Those people findings agree with the intuition one of these actions they is important one as often intellectual running that you can is mirrored in the cursor actions. Specifically, persisted regression ways assume the same group of cognitive responses is actually going on within the exact same part of the trajectory across products. In order to meet so it presumption, a similar part of intellectual answering should be completed inside trajectory so that the cognition–trajectory positioning are consistent. Actually, including alignment issues in addition to develop in the interpreting enjoy-relevant sensory potentials during the cognitive handling (age.g., Jackson & Bolger, 2014).
Information per aspect of so it intricate processes is the key for those, cyber security choice-producers, and you may organizations seeking fortify the defences. Zero-mouse click periods depict a good paradigm change within the cyber protection, requiring heightened feeling and you can hands-on defences. It’s very obvious one an intensive knowledge of this type of episodes is important for folks, organisations, and cyber defense pros the exact same. Paul states regulators officials fooled the public from the You.S. funding away from lookup inside the Wuhan, Asia. He and you will Family Republicans have looked at NIH funding away from pathogen-changing look in the Wuhan Institute from Virology and you will due to provides to your EcoHealth Alliance. The new libertarian senator is considered the most singing experts out of researchers and you will technology organizations, for instance the Federal Education from Health and previous better infectious condition researcher Anthony Fauci.




